We are given a packet capture that you can find here: communication.pcap
We also get a hint: “Let's call someone from the old days”
The capture contains a RTP communication that we can listen using Wireshark:

One of the streams got us Rickrolled XDDD, but the other one sounded like some kind of binary data communication. The last one looks like a FSK:
And this is its frequency distribution, with peaks in 1100Hz and 2300Hz:

So we google a bit, searching for FSK, 1100 and 2300 Hz and we got here:
http://www.herrera.unt.edu.ar/eiii/material/apuntes/FMEstereo-ModEspeciales.pdf

Which directed us to Bell 202 modems, and to AX.25 modulation, which is supported by SkySweeper, so after changing baud rate to 1200 we get a familiar output (It’s difficut to describe how happy a PNG header can make you after some trial and error
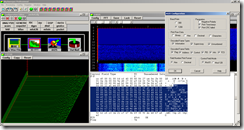
These are the packets with the png file:
FRAME TYPE : Unnumbered Frame
Flag : 7e
Destination Address : NOCALL 60
Source Address : OTA22 61
Control Field Type : UI Unnumbered Information
P/F : 0
cc 45 00 01 00 fd cf 40 00 40 06 27 ce 0a 2b 00 LE...}O@.@.'N.+.
01 0a 2b 00 04 9a d8 27 0f a9 fd 3f 7d 7a 0c d3 ..+...X'.)}?}z.S
bd 80 10 00 08 ad bf 00 00 01 01 08 0a 04 a7 c4 =....-?.......'D
f6 00 12 a5 e4 89 50 4e 47 0d 0a 1a 0a 00 00 00 v..%d.PNG.......
0d 49 48 44 52 00 00 00 af 00 00 00 af 01 03 00 .IHDR.../.../...
00 00 b1 5c 1c 36 00 00 00 06 50 4c 54 45 ff ff ..1\.6....PLTE..
ff 00 00 00 55 c2 d3 7e 00 00 01 a3 49 44 41 54 ....UBS~...#IDAT
48 89 bd 97 c1 b1 83 30 0c 44 37 93 83 8f 94 e0 H.=.A1.0.D7....`
4e a0 31 66 60 26 8d 41 27 94 c0 91 03 83 fe ae N 1f`&.A'.@...~.
cc cf ff 0d 2c 3e 38 f0 cc c1 96 56 6b 05 78 7e LO..,>8pLA.Vk.x~
94 e0 c0 b0 bf 73 da ca aa f7 c5 8b 17 a0 e2 45 .`@0?sZJ*wE.. bE
cc a7 11 65 dd 21 66 c5 6b 9c 15 3d 49 5c 98 36 L'.e]!fEk..=I\.6
7e 30 c5 13 98 bf d3 a6 3d e1 31 8c 57 9c 88 a5 ~0E..?S&=a1.W..%
fb 6c c7 13 58 f1 e6 c4 ec de f8 2f 0d 2e 2c 15 {lG.XqfDl^x/..,.
31 b1 63 bd a7 7f 62 33 e1 56 29 ab 84 cc 08 d4 11c='.b3aV)+.L.T
5f 62 c5 c3 2e 21 c7 67 0b 69 38 9f dc b8 67 a8 _bEC.!Gg.i8.\8g(
e3 c
FCS : 40c6 OK
Flag : 7e
FRAME TYPE : Unnumbered Frame
Flag : 7e
Destination Address : NOCALL 60
Source Address : OTA22 61
Control Field Type : UI Unnumbered Information
P/F : 0
cc 45 00 01 00 fd d0 40 00 40 06 27 cd 0a 2b 00 LE...}P@.@.'M.+.
01 0a 2b 00 04 9a d8 27 0f a9 fd 40 49 7a 0c d3 ..+...X'.)}@Iz.S
bd 80 10 00 08 f7 ac 00 00 01 01 08 0a 04 a7 c4 =....w,.......'D
f6 00 12 a5 e4 ea 66 85 a1 c5 bb 1e 66 3c 50 46 v..%djf.!E;.f<PF
b9 76 80 6b dc 4e aa ca 89 95 62 12 bc e3 5b ae 9v.k\N*J..b.<c[.
7a 75 e2 f4 23 96 cd 5c 8f be 53 d0 f9 95 36 68 zubt#.M\.>SPy.6h
c4 ac 98 19 8c f2 fb 76 08 70 cd 8c 35 24 5f 9e D,...r{v.pM.5$_.
5b e4 18 62 86 1b f7 dd 99 3b 51 bc 53 50 53 13 [d.b..w].;Q<SPS.
b2 0f eb f0 95 42 fe 84 d4 5c ff ee 1d 23 ce 8a 2.kp.B~.T\.n.#N.
e9 3b 3a 53 d0 21 0e 95 ab 19 33 ca dc 49 30 c5 i;:SP!..+.3J\I0E
b9 c6 08 8c d5 8c ef fb ba 5d 30 a9 66 8a 0c 56 9F..U.o{:]0)f..V
8c 41 77 1a cb 75 e3 53 fa 3e 3d 6a 71 63 16 69 .Aw.KucSz>=jqc.i
b4 28 f3 dc 19 7e 58 71 09 79 2d fb 93 9a a6 c4 4(s\.~Xq.y-{..&D
c3 67 ef e0 c4 39 98 e2 29 58 a9 27 ca 85 76 78 Cgo`D9.b)X)'J.vx
23 2e 92 11 77 92 96 af 0f 32 d9 56 9c 83 35 1b #...w../.2YV..5.
cd 75 43 22 33 e3 d6 51 eb 82 41 5a a0 ee 34 37 MuC"3cVQk.AZ n47
5e ^
FCS : 7b57 OK
Flag : 7e
FRAME TYPE : Unnumbered Frame
Flag : 7e
Destination Address : NOCALL 60
Source Address : OTA22 61
Control Field Type : UI Unnumbered Information
P/F : 0
cc 45 00 00 8a fd d1 40 00 40 06 28 42 0a 2b 00 LE...}Q@.@.(B.+.
01 0a 2b 00 04 9a d8 27 0f a9 fd 41 15 7a 0c d3 ..+...X'.)}A.z.S
bd 80 18 00 08 02 ba 00 00 01 01 08 0a 04 a7 c4 =.....:.......'D
f6 00 12 a5 e4 d4 51 d3 75 19 ef 3d 1b ce 69 2b v..%dTQSu.o=.Ni+
66 dc 7a 4d 92 54 b3 f6 95 29 7e 02 87 24 8d af f\zM.T3v.)~..$./
29 b9 71 76 b6 32 25 65 77 ac 61 c6 8a b7 3a db )9qv62%ew,aF.7:[
d6 02 96 8b fa 4a 9d 19 f1 fd 1f 10 cd 7f 39 cd V...zJ..q}..M.9M
df 26 de 84 9f 1f 3f 12 35 c5 cb 56 7f cb c1 00 _&^...?.5EKV.KA.
00 00 00 49 45 4e 44 ae 42 60 82 ...IEND.B`.
FCS : 9967 OK
Flag : 7e
Since there are only a few packets, we reconstructed the stream from the packets manually to get a QR-Code…

… which gives us the key:
The key is: 73e4geru3i21eWuypzFIueK

No hay comentarios:
Publicar un comentario